SSTI to Local File Read
This blog post is about a Server Side Template Injection that i found few months ago on a private program and i was able
to read local files through it. Unfortunately, i was unable to escalte it to rce but it was fun exploiting it.
Web Applications mostly use template engines to dynamically generate webpage or emails. These Template engines allow embedding
users input into the web application. Server-Side Template injections occur when a web application accepts input from users
without sanitizing it properly.
So i was invited to this program which was related to hiring people for home improvements, construction etc. Only main domain was
in scope, XSS and CSRF were out-of-scope becuase they were site-wide known issues which narrowed down the possibility of getting bugs
to 25% for me,lol. Nevertheless, i created an
account and started exploring the functionalities on the web app. The app was very small with only few pages and only two,three pages
were interested enough. I found some xss to motivate myself that i can find some other bugs too. After going through the web app as
a normal user i started poking around. I started from the Edit Profile page as CSRF was out of scope i tried looking for idor and
file uploads bugs but couldn't get any. I noticed that special charaters are allowed in your name and the only thing came into my mind
was testing it for Server Side Template Injection (ssti).
I simple changed my name to {{7*'7'}} test and saved it. And now it was time to see if 49 test is reflecting somewhere on the app but
it wasnt. The last place where it could reflect is in the email, so i went to the forget password page and asked for a password reset
email. When i got my email the ssti payload was executing in there and i saw Hello 49, in the password reset email.
This looked straightaway like an SSTI vulnerability. When i saw that i started spraying ssti payloads blindly and praying for them
to work and give me p1 in 5 minutes lol, but it didnt work obviously. I had very little knowledge about ssti at that time so i went to
google and did some research about ssti.
To exploit ssti, first we need to identify which back-end template engine is being used. To detect the running back-end template engine
we can use some different ssti payloads and can guess the template engine from the respone we get from the server.
After some trial and erros, i gussed that Twig is being used by the back-end. After finding this out i tried some payloads for Twig but
they still didnt work, i was getting empty emails for some payloads, the payloads i used are:
{{['id']|filter('system')}} = no email or empty email
"{{'/etc/passwd'|file_excerpt(1,30)}}"@ = no email or empty email
{{['cat\x20/etc/passwd']|filter('system')}} = no email or empty email
After doing some more research i realized the template engine might be running in a sandboxed environment. I tried some bypasses but they
didnt work. Now it was the time to read twig's documentation, after reading it i started trying to use those fuctions mentioned there. Most
of the functions are resulting in no emails or empty emails. But finally i tried the function {{source}} and was able to read
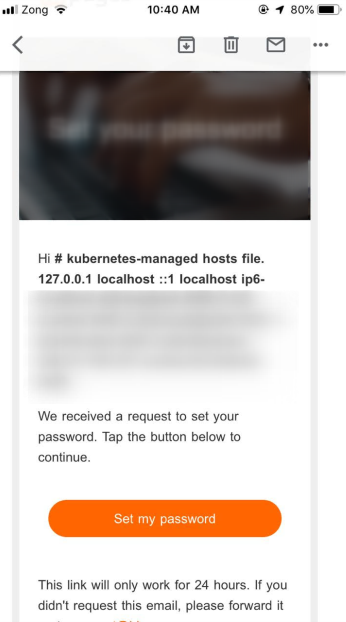
the local files, like this {{source("\etc\hosts")}}, as you can see in the image below. I submitted the report and the program owner trigaed it as p3 but later it was
rewarded as p2.
I wanted to thank my friend m0pp1 for helping me with the exploitation.
If you made it to here i also wanted to thank you for reading it. If you want to give me a feedback of
any kind, feel free to reach me at my Twitter.
See you in the next article.